Vendor: Cisco
Certifications: CCNA Security
Exam Name: Implementing Cisco Network Security
Exam Code: 210-260
Total Questions: 186 Q&As
Exam Information:http://www.leads4pass.com/210-260.html
Lead4pass 210-260 PDF: Implementing Cisco Network Security
- 235 Questions With Answers
- Updation Date : 20 Apr 2017
- 210-260 Real Exams Question Answers
- Just 1 day study required to pass exam
- 100% Passing Assurance
- Money Back Guarantee
- Free 3 Months Updates
Cisco Certified Network Associate Security (CCNA Security) validates associate-level knowledge and skills required to secure Cisco networks. With a CCNA Security certification, a network professional demonstrates the 210-260 pdf skills required to develop a security infrastructure, recognize threats and vulnerabilities to networks, and mitigate security threats.
♥♥Lead4pass Latest and Most Accurate Cisco 210-260 PDF Exam Q&As ♥♥
QUESTION 20 Refer to the exhibit.
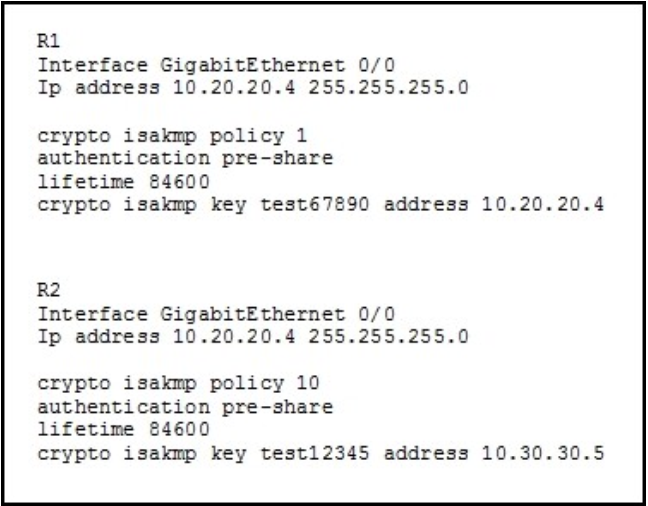
You have configured R1 and R2 as shown, but the routers are unable to establish a site-to- site VPN
tunnel. What action can you take to correct the problem?
A. Edit the crypto keys on R1 and R2 to match.
B. Edit the ISAKMP policy sequence numbers on R1 and R2 to match.
C. Set a valid value for the crypto key lifetime on each router.
D. Edit the crypto isakmp key command on each router with the address value of its own interface.
Correct Answer: A
QUESTION 21
What is an advantage of implementing a Trusted Platform Module for disk encryption?
A. It provides hardware authentication.
B. It allows the hard disk to be transferred to another device without requiring re- encryption.dis
C. It supports a more complex encryption algorithm than other disk-encryption technologies.
D. It can protect against single points of failure.
Correct Answer: A
QUESTION 22
Refer to the exhibit
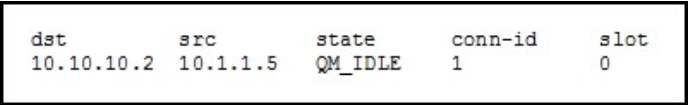
While troubleshooting site-to-site VPN, you issued the show crypto isakmp sa command.
What does the given output show?
A. IPSec Phase 1 is established between 10.10.10.2 and 10.1.1.5.
B. IPSec Phase 2 is established between 10.10.10.2 and 10.1.1.5.
C. IPSec Phase 1 is down due to a QM_IDLE state.
D. IPSec Phase 2 is down due to a QM_IDLE state.
Correct Answer: A
QUESTION 23
What is the purpose of the Integrity component of the CIA triad?
A. to ensure that only authorized parties can modify data
B. to determine whether data is relevant
C. to create a process for accessing data
D. to ensure that only authorized parties can view data
Correct Answer: A
QUESTION 24
Which statements about smart tunnels on a Cisco firewall are true? (Choose two.)
A. Smart tunnels can be used by clients that do not have administrator privileges
B. Smart tunnels support all operating systems
C. Smart tunnels offer better performance than port forwarding
D. Smart tunnels require the client to have the application installed locally
Correct Answer: AC
QUESTION 25
What is the FirePOWER impact flag used for?
A. A value that indicates the potential severity of an attack.
B. A value that the administrator assigns to each signature.
C. A value that sets the priority of a signature.
D. A value that measures the application awareness.
Correct Answer: A 210-260 pdf
QUESTION 26
What are the three layers of a hierarchical network design? (Choose three.)
A. access
B. core
C. distribution
D. user
E. server
F. Internet
Correct Answer: ABC
QUESTION 27
What is the best way to confirm that AAA authentication is working properly?
A. Use the test aaa command.
B. Ping the NAS to confirm connectivity.
C. Use the Cisco-recommended configuration for AAA authentication.
D. Log into and out of the router, and then check the NAS authentication log.
Correct Answer: A
QUESTION 28
Which operating system is supported by the BlackBerry MVS? (Choose one.)
A. Windows Server 2003 R1 SP1 Enterprise Edition
B. Windows Server 2003 R2 SP2 Standard Edition
C. Ubuntu Server 4.0
D. Windows Server 2000 R2 SP2
E. Windows 7 Professional Edition
Correct Answer: B
QUESTION 29
When a BlackBerry MVS user moves a call from the BlackBerry device to the desk phone, the person they are speaking to is redirected to the user’s voice mail. What is the cause of this issue? (Choose one.)
A. No data channel to complete the transfer
B. Off-hook desk phone of the person the user is speaking to
C. The busy trigger on the PBX is set to less than 3
D. The wireless network fails to send the calls to the desk phone
Correct Answer: C
QUESTION 30
Which configuration is a valid implementation of BlackBerry MVS high availability? (Choose one.)
A. Two active BlackBerry MVS Session Managers and one BlackBerry MVS Console
B. Two BlackBerry MVS Session Managers and two BlackBerry MVS Consoles
C. Oneactive BlackBerry MVS Session Manager, one standby BlackBerry MVS Session Manager and one BlackBerry MVS Console
D. Twoactive BlackBerry MVS Session Managers and two BlackBerry MVS Consoles
E. Oneactive BlackBerry MVS Session Manager, one standby BlackBerry MVS Session Manager and two BlackBerry MVS Consoles
Correct Answer: C
This 210-260 pdf with 11 chapters emphasizes core security technologies, the installation, troubleshooting and monitoring of network devices to maintain integrity, confidentiality and availability of data and devices, and competency in the technologies that Cisco uses in its security structure.
210-260 pdf topics for the course include Secure Access, Cisco ASA, Firewalls, IPS/IDS, VPNs and Secure Routing and Switch. Join thousands of other IT Professionals, achieve your goals and get started today working towards you CCNA Security certification!
210-260 PDF Training Materials Detail:http://www.leads4pass.com/210-260.html
Official Site: http://www.cisco.com/c/en/us/training-events/training-certifications/exams/current-list/iins-210-260.html
https://youtu.be/EZTrv1txQQc



