The latest and most comprehensive 350-701 exam dumps help you pass the exam with ease. So if you want to pass the exam, you must get the latest 350-701 exam dumps in 2023.
Pass4itSure has just updated the 350-701 exam dumps 2023 https://www.pass4itsure.com/350-701.html with the latest real exam materials to power the 350-701 SCOR exam.

Is the 350-701 SCOR exam really hard to pass?
Passing the 350-701 SCOR exam requires serious study, you need to master the basic content of the exam, obtain the latest exam materials, and carefully practice the exam questions so that the 350-701 SCOR exam is not difficult.
There are 90-110 questions in the real 350-701 exam, and you need to answer them in 120 minutes and get a score of 750-850 to pass. It costs $400 to take the exam.
What is the smartest way to prepare for the Implementing and Operating Cisco Security Core Technologies (SCOR) exam?
Use the latest 350-701 exam dumps in 2023.
Where can I get valid 350-701 exam dumps in 2023?
The Pass4itSure website has it for you. Pass4itSure updated the 350-701 exam dumps 2023 is the medicine to successfully pass the Cisco 350-701 SCOR exam.
Where to provide the latest Cisco CCNP 350-701exam questions or dumps PDF downloads, for free?
Certadept.com offers you free 350-701 exam questions, which you can check below.
[google drive] download free 350-701 pdf: https://drive.google.com/file/d/1wg00K7yyP0VR2xnS9xTBMmNhNVQkFIP9/view?usp=share_link
Latest Cisco 350-701 (SCOR) Free Dumps Questions | 2023
New Q1
An organization recently installed a Cisco WSA and would like to take advantage of the AVC engine to allow the organization to create a policy to control application-specific activity. After enabling the AVC engine, what must be done to implement this?
A. Use security services to configure the traffic monitor,
B. Use URL categorization to prevent application traffic.
C. Use an access policy group to configure application control settings.
D. Use web security reporting to validate engine functionality
Correct Answer: C
The Application Visibility and Control (AVC) engine lets you create policies to control application activity on the network without having to fully understand the underlying technology of each application. You can configure application control settings in Access Policy groups. You can block or allow applications individually or according to application type. You can also apply controls to particular application types.
New Q2
An engineer integrates Cisco FMC and Cisco ISE using pxGrid. Which role is assigned to Cisco FMC?
A. client
B. server
C. controller
D. publisher
Correct Answer: D
New Q3
Which security product enables administrators to deploy Kubernetes clusters in air-gapped sites without needing Internet access?
A. Cisco Content Platform
B. Cisco Container Controller
C. Cisco Container Platform
D. Cisco Cloud Platform
Correct Answer: C
New Q4
How does the Cisco WSA enforce bandwidth restrictions for web applications?
A. It implements a policy route to redirect application traffic to a lower-bandwidth link.
B. It dynamically creates a scavenger class QoS policy and applies it to each client that connects through the WSA.
C. It sends commands to the uplink router to apply traffic policing to the application traffic.
D. It simulates a slower link by introducing latency into application traffic.
Correct Answer: C
New Q5
A hacker initiated a social engineering attack and stole the usernames and passwords of some users within a company. Which product should be used as a solution to this problem?
A. Cisco NGFW
B. Cisco AnyConnect
C. Cisco AMP for Endpoints
D. Cisco Duo
Correct Answer: D
New Q6
Which two criteria must a certificate meet before the WSA uses it to decrypt application traffic? (Choose two.)
A. It must include the current date.
B. It must reside in the trusted store of the WSA.
C. It must reside in the trusted store of the endpoint.
D. It must have been signed by an internal CA.
E. it must contain a SAN.
Correct Answer: AB
New Q7
Which Cisco platform processes behavior baselines, monitors for deviations, and reviews for malicious processes in data center traffic and servers while performing software vulnerability detection?
A. Cisco Tetration
B. Cisco ISE?
C. Cisco AMP for Network
D. Cisco AnyConnect
Correct Answer: A
New Q8
Refer to the exhibit.
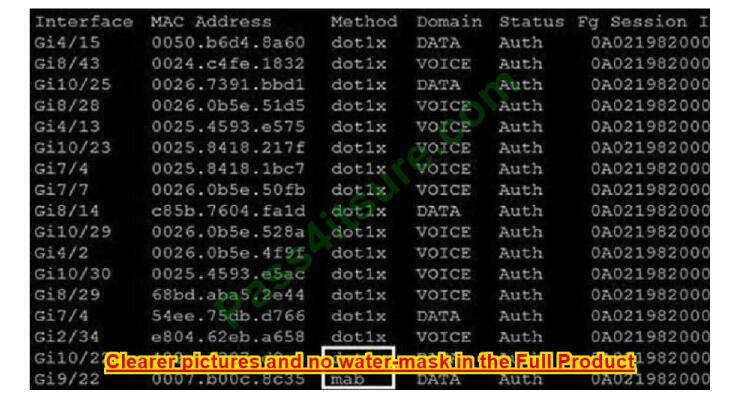
Which command was used to generate this output and to show which ports are authenticating with dot1x or mab?
A. show authentication registrations
B. show the authentication method
C. show dot1x all
D. show authentication sessions
Correct Answer: D
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/security/s1/sec-s1-xe-3se- 3850-cr-book/sec-s1-xe-3se3850-cr-book_chapter_01.html#wp3404908137 Displaying the Summary of All Auth Manager Sessions on the Switch Enter the following:
Switch# show authentication sessions Interface MAC Address Method Domain Status Session ID Gi1/48
0015.63b0.f676 dot1x DATA Authz Success 0A3462B1000000102983C05C Gi1/5 000f.23c4.a401 mab DATA Authz Success 0A3462B10000000D24F80B58 Gi1/5 0014.bf5d.d26d dot1x DATA Authz Success
0A3462B10000000E29811B94
New Q9
Which type of protection encrypts RSA keys when they are exported and imported?
A. file
B. passphrase
C. NGE
D. nonexportable
Correct Answer: B
New Q10
What is the benefit of using Cisco CWS compared to an on-premises Cisco WSA?
A. Cisco CWS eliminates the need to backhaul traffic through headquarters for remote workers whereas Cisco WSA does not
B. Cisco CWS minimizes the load on the internal network and security infrastructure as compared to Cisco WSA.
C. URL categories are updated more frequently on Cisco CWS than they are on Cisco WSA
D. Content scanning for SAAS cloud applications is available through Cisco CWS and not available through Cisco WSA
Correct Answer: A
New Q11
Which Cisco solution does Cisco Umbrella integrate with to determine if a URL is malicious?
A. AMP
B. AnyConnect
C. DynDNS
D. Talos
Correct Answer: D
When Umbrella receives a DNS request, it uses intelligence to determine if the request is safe, malicious, or risky — meaning the domain contains both malicious and legitimate content. Safe and malicious requests are routed as usual or blocked, respectively. Risky requests are routed to our cloud-based proxy for deeper inspection. The Umbrella proxy uses Cisco Talos web reputation and other third-party feeds to determine if a URL is malicious.
New Q12
Which feature enables a Cisco ISR to use the default bypass list automatically for web filtering?
A. filters
B. group key
C. company key
D. connector
Correct Answer: D
New Q13
What are two reasons for implementing a multifactor authentication solution such as Duo Security provides to an organization? (Choose two)
A. flexibility of different methods of 2FA such as phone callbacks, SMS passcodes, and push notifications
B. single sign-on access to on-premises and cloud applications
C. integration with 802.1x security using native Microsoft Windows supplicant
D. secure access to on-premises and cloud applications
E. identification and correction of application vulnerabilities before allowing access to resources
Correct Answer: AD
Two-factor authentication adds a second layer of security to your online accounts. Verifying your identity using a second factor (like your phone or another mobile device) prevents anyone but you from logging in, even if they know your password.
Note: Single sign-on (SSO) is a property of identity and access management that enables users to securely authenticate with multiple applications and websites by logging in only once with just one set of credentials(username and password). With SSO, the application or website that the user is trying to access relies on a trusted third party to verify that users are who they say they are.
Summarize:
The latest 350-701 exam dumps can help crack exams, especially those provided by Pass4itSure. You can use the latest 350-701 dumps https://www.pass4itsure.com/350-701.html easily pass the Cisco 350-701 SCOR exam in 2023.



