Should I take Cisco 300-370 dumps? “Troubleshooting Cisco Wireless Enterprise Networks” is the name of Cisco 300-370 exam dumps which covers all the knowledge points of the real Cisco exam. New Updated Cisco 300-370 dumps pdf Cisco Wireless Enterprise Networks exam video for your excellence.Pass4itsure Cisco 300-370 dumps exam questions answers are updated (60 Q&As) are verified by experts.
The associated certifications of 300-370 dumps is CCNP Wireless. Pass4itsure is a globally renowned organization for Cisco Certified Network Professional Wireless https://www.pass4itsure.com/300-370.html dumps of specialized Troubleshooting Cisco Wireless Enterprise Networks exam dumps. Further about 1.5 million Candidates in over 120 countries obtain certification by Pass4itsure 300-370 exam preparation materials.
Exam Code: 300-370
Exam Name: Troubleshooting Cisco Wireless Enterprise Networks
Q&As: 60
[2017-NEW Cisco 300-370 Dumps From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWVVhaZUpnZWRvOHM
[2017-NEW Cisco 400-101 Dumps From Google Drive]:https://drive.google.com/open?id=0BwxjZr-ZDwwWczJDVzl1SUJLWms

Pass4itsure Latest and Most Accurate Cisco 300-370 Dumps Exam Q&As:
QUESTION 27
A mobile station in a factory contains an AP configured as a work group bridge that authenticates to a root
AP using EAP-FAST. To be able to use the mobile station in further parts of the factory, another root AP is
installed and also configured for EAP-FAST When the mobile station is attempting to roam to the other AP,
it loses connection yet can still authenticate to the first one. What is the cause for the failed authentication
on RAP2?
Refer to the exhibit.
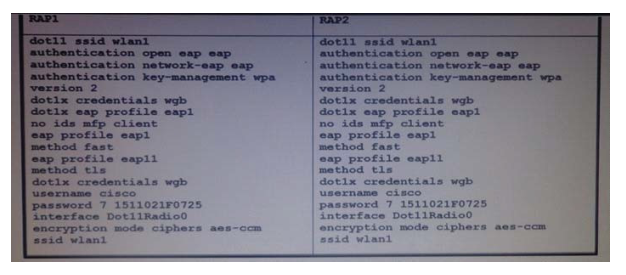
A. RAP1 is using a different authentication protocol than RAP2.
B. RAP2 has a different SSID than RAP1.
C. RAP1 is using a different encryption than RAP2.
D. The authentication use name and password is different.
300-370 exam Correct Answer: A
QUESTION 28
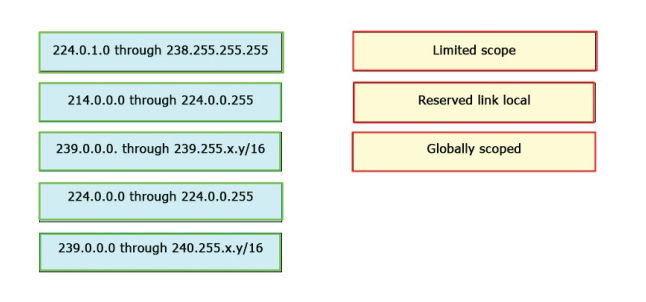
DRAG DROP
Drag and drop the IP address range on the left onto the specific purpose for multicast groups on the right.
Not all options are used.
Select and Place:
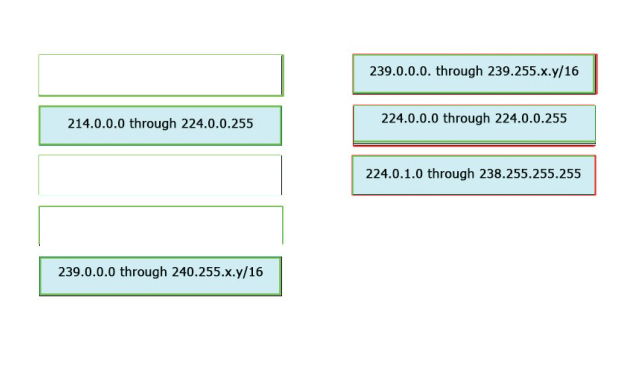
Correct Answer:
QUESTION NO: 29
Which of the following attributes of the customErrors element is used to specify whether custom
errors are enabled, disabled, or shown only to remote clients?
A. Off
B. Mode
C. On
D. RemoteOnly
300-370 dumps Answer: B
QUESTION NO: 30
What is the main purpose of a try-catch block?
A. To obtain and use resources that are being caught.
B. To signal the occurrence of an exception during the program execution.
C. To catch and handle an exception generated by an executable code.
D. To ensure that the necessary cleanup of external resources is done immediately.
Answer: C
QUESTION NO: 31
ASP.NET version 2.0 health monitoring supports an __________.
A. Event driven model
B. Event provider model
C. Event log model
D. Event API model
300-370 pdf Answer: B
QUESTION NO: 32
Which of the following APIs is used to collect information about any running state and any errors
that occur within an ASP.NET application?
A. Profile API
B. Health Monitoring API
C. Error Handling API
D. Personalization API
Answer: B
QUESTION NO: 33
The <customErrors> element does not apply to errors that occur in __________.
A. XML Web services
B. Windows services
C. Web services directory
D. Web services
300-370 vce Answer: A
QUESTION NO: 34
Which of the following syntaxes is used for the EncryptionAlgorithm property of the Message
class?
A. [MessagingDescriptionAttribute(“MessageEncryptionAlgorithm”)]
public EncryptionAlgorithm : EncryptionAlgorithm { }
B. [MessagingDescriptionAttribute(“MessageEncryption”)]
public EncryptionAlgorithm EncryptionAlgorithm { }
C. [MessagingDescriptionAttribute(“MessageEncryption”)]
public EncryptionAlgorithm EncryptionAlgorithm { get; set; }
D. [MessagingDescriptionAttribute(“MessageEncryptionAlgorithm”)]
public EncryptionAlgorithm : EncryptionAlgorithm { get; set; }
Answer: C
QUESTION NO: 35
Which of the following is the best encryption algorithm to encrypt and decrypt messages?
A. AES
B. TripleDES
C. DES
D. RSA
300-370 exam Answer: D
QUESTION NO: 36
Which of the following is not a method of controlling traffic through a firewall?
A. Application filtering
B. Encryption-level filtering
C. Stateful inspection
D. Packet filtering
Answer: B
QUESTION NO: 37
Which of the following algorithms supports key lengths from 128 bits to 192 bits in increments of
64 bits?
A. DESCryptoServiceProvider
B. TripleDESCryptoServiceProvider
C. TripleDES
D. AESCryptoServiceProvider
300-370 dumps Answer: C
QUESTION NO: 38
Which of the following provide simplified access to ASP.NET AJAX login, roles, and profile
services from Windows Forms and WPF applications?
A. Entity Framework
B. AJAX application services
C. Client application services
D. Sync Framework
Answer: C
QUESTION NO: 39
Which of the following providers is a block cipher that encrypts and decrypts data in blocks of 8
bytes?
A. RNGCryptoServiceProvider
B. SHA1CryptoServiceProvider
C. RC2CryptoServiceProvider
D. RSACryptoServiceProvider
300-370 pdf Answer: C
QUESTION NO: 40
Which of the following is required to be implemented by marshal-by-value objects to implement
custom serialization rules?
A. ISerializable
B. SerializableAttribute
C. ISerializableAttribute
D. ISerialize
Answer: A
QUESTION NO: 41
Which of the following is not a type of Remote object?
A. Server-activated object
B. Client-activated object
C. Singleton object
D. Single call object
300-370 vce Answer: A
QUESTION NO: 42
Which of the following is an exception of background threads as compared to foreground threads?
A. A background thread does not continue the managed execution environment running.
B. A background thread does not affect the outcome of an unhandled exception.
C. A background thread belongs to the managed thread pool.
D. A background thread changes to a foreground thread at any time.
Answer: A
QUESTION NO: 43
Which of the following classes limits the number of threads that can access a resource or pool of
resources concurrently?
A. Semaphore
B. Mutex
C. Thread
D. Monitor
300-370 exam Answer: A
QUESTION NO: 44
Which of the following is TRUE about a managed thread?
A. It is a foreground thread.
B. It is a managed assembly.
C. It is either a background thread or a foreground thread.
D. It is a background thread.
Answer: C
QUESTION NO: 45
Which of the following security methods is used when the code requires a specific set of
permissions, which are not known until runtime?
A. Role-Based Security
B. Windows NT Security
C. Imperative Security
D. Declarative Security
300-370 dumps Answer: C
QUESTION NO: 46
All of the following are benefits for query expressions allowed by Language-integrated query
except for which one?
A. Rich metadata
B. Compile-time syntax checking
C. Static typing and IntelliSense
D. Imperative code
Answer: D
QUESTION NO: 47
Which class allows checks against the active principal using the language constructs defined for
the declarative and imperative security actions?
A. IPrincipal
B. CodeAccessPermission
C. PrincipalPermission
D. SecurityPermission
300-370 pdf Answer: C
QUESTION NO: 48
Which of the following elements will you use to add a script to the ScriptManager declaratively?
A. <connectionStrings>
B. <Scripts>
C. <configuration>
D. <script>
Answer: B
With assessment based on principles, best details and frameworks Pass4itsure offers highest worth Cisco Certified Network Professional Wireless 300-370 dumps review and services to steps forward the careers of specialized persons within https://www.pass4itsure.com/300-370.html dumps Cisco Certified Network Professional Wireless exam.



